Wow, an iPhone exploit with no user interaction, and thanks NSA for all the fish? DarkMatter applied for inclusion in Mozilla, too..
Category: Thoughts
Simple read-only git repository over HTTP
I’m working on a code exercise and wanted to throw it in a web directory to allow read-only git clone/pull, without putting the repo up as a public one on github. Initializing the repository and using SSH for read-write access was familiar, since I’ve done it many times, but I stumbled around for a few minutes scanning docs for read-write HTTP repos that use fastcgi, gitweb, git-http-backend, git daemon, etc. This is just using simple and “dumb” read-only HTTP access, and the tidbit I had long forgotten was enabling the post-update hook to update the repository metadata, which just execs git update-server-info as commits are made – of course, git needs to be installed on the web server.
$HTTPROOT is the full path to your website directory (i.e. /srv/http/example.com).
On the server:
$ mkdir -p $HTTPROOT/git/myrepo.git
$ cd $HTTPROOT/git/myrepo.git/
$ git init --bare
$ mv hooks/post-update.sample hooks/post-update
On the client, use SSH to clone the repository for read-write work (needs full path to $HTTPROOT):
$ git clone ssh://$HOST/$HTTPROOT/git/myrepo.git
Cloning into 'myrepo'...
warning: You appear to have cloned an empty repository.
Checking connectivity... done
$ cd myrepo/
Then go about adding files, committing, and pushing changes over SSH.
When it comes time to share your work, the read-only repository can be shared with others and cloned/pulled with:
$ git clone http://$HOST/git/myrepo.git
Cloning into 'myrepo'...
Checking connectivity... done
The Battle for Power on the Internet
Recently, Bruce Schneier was interviewed by Technology Review on the NSA and the Snowden documents. The last question in the interview is brilliant. I have difficulty trying to explain to non-geeks that there are ways to maintain privacy, but since the methods require knowledge that typical Internet users don’t possess, online privacy is out of reach. The learning curve is too steep. Bruce nails it:
So you’ve recently suggested five tips for how people can make it much harder, if not impossible, to get snooped on. These include using various encryption technologies and location-obscuring methods. Is that the solution?
My five tips suck. They are not things the average person can use. One of them is to use PGP [a data-encryption program]. But my mother can’t use PGP. Maybe some people who read your publication will use my tips, but most people won’t.
Basically, the average user is screwed. You can’t say “Don’t use Google”—that’s a useless piece of advice. Or “Don’t use Facebook,” because then you don’t talk to your friends, you don’t get invited to parties, you don’t get laid. It’s like libertarians saying “Don’t use credit cards”; it just doesn’t work in the real world.
The Internet has become essential to our lives, and it has been subverted into a gigantic surveillance platform. The solutions have to be political. The best advice for the average person is to agitate for political change.
Today, Bruce posted a link to his TEDxCambridge talk from last week and further explains the above idea, how the Internet has evolved to the current state, and what sorts of things will need to happen over the next decades to preserve its usefulness for humanity. If you use the Internet, this is 12 minutes of must see insight..
The web of (dis)trust is growing.
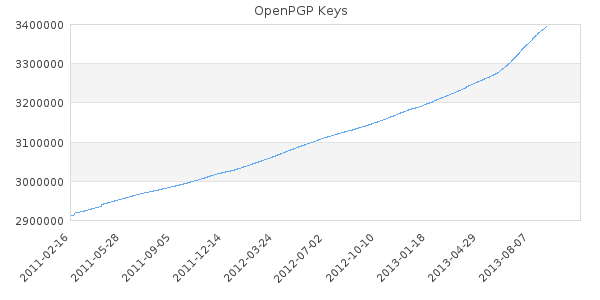
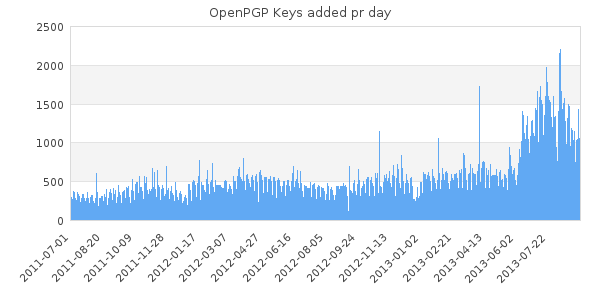
The growth of the number of new OpenPGP keys seen on sks-keyservers.net has been very steady, until a few months ago. The increase is fairly dramatic as people are beginning to see the need to secure their communications. Tie this in with the last few months of (in)security news and it appears that people are getting the message that they need to actively use the tools available to to them, if they wish to keep at least a few tidbits of private information from prying eyes.
https://sks-keyservers.net/status/key_development.php
Public Prediction: CAs will be named..
Public prediction: One of the next NSA revelations will be the names of the SSL/TLS Certificate Authorities that gave up private keys.